Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Ray DoyleRay Doyle is an avid pentester/security enthusiast/beer connoisseur who has worked in IT for almost 16 years now. From building machines and the software on them, to breaking into them and tearing it all down; he’s done it all.…

Ray DoyleRay Doyle is an avid pentester/security enthusiast/beer connoisseur who has worked in IT for almost 16 years now. From building machines and the software on them, to breaking into them and tearing it all down; he’s done it all.…

If you prefer guided learning, then cyber security certifications might be the best choice for you! Ray DoyleRay Doyle is an avid pentester/security enthusiast/beer connoisseur who has worked in IT for almost 16 years now. From building machines and the…
If you are a member of the “learn by doing” crowd, then these resources can help you practice hacking with a hands-on approach. Ray DoyleRay Doyle is an avid pentester/security enthusiast/beer connoisseur who has worked in IT for almost 16…

If you’ve never been to any cyber security conferences, then hopefully this can convince you! Ray DoyleRay Doyle is an avid pentester/security enthusiast/beer connoisseur who has worked in IT for almost 16 years now. From building machines and the software…

With DerbyCon canceled, I wanted to combine all of my yearly posts into one memoir. Ray DoyleRay Doyle is an avid pentester/security enthusiast/beer connoisseur who has worked in IT for almost 16 years now. From building machines and the software…
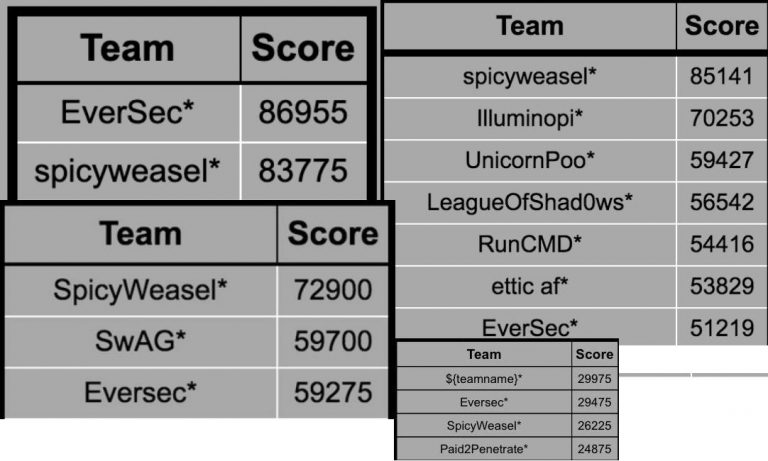
Want to learn more about capture the flag hacking competitions? Don’t even know what CTF stands for? Or just want to know how to win a ton of awesome prices and knowledge? If so, then you are in the right…

While I know this may not be the preferred spelling, I want to repurpose ALL of my old DEFCON convention posts, so here we go! Ray DoyleRay Doyle is an avid pentester/security enthusiast/beer connoisseur who has worked in IT for…

I wanted to update and combine some of my hacker conference posts, so BSidesRDU made for a great first run at it! Ray DoyleRay Doyle is an avid pentester/security enthusiast/beer connoisseur who has worked in IT for almost 16 years…
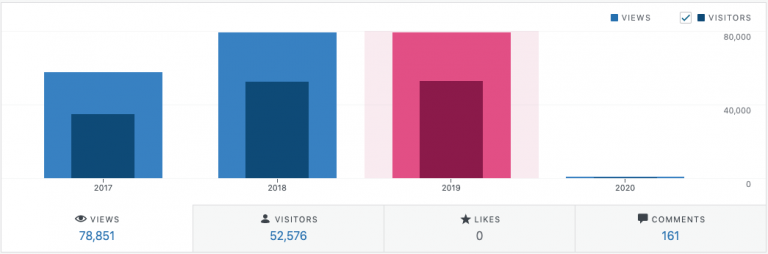
It was time for me to combine all of my hacking blog updates and statuses so that I’d have one living post! Ray DoyleRay Doyle is an avid pentester/security enthusiast/beer connoisseur who has worked in IT for almost 16 years…