Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Since I wanted to extend the break from my assembly journey, I figured I would share my HELK installation and configuration guide.
If you read my DEF CON post this year, then you know I took the SpecterOps Adversary Tactics: Red Team Operations course.
During this course, the instructors were using HELK (among other things), to do their hunting of us. After talking with Brian and Will after the course, I decided to set up instance of it in my home lab. I’d never done blue-team work before and only performed true stealthy assessments a few times in my career.
Setting up and using HELK will not only allow me to see what the hunters see but also improve my tradecraft!
First, I set up a new VM for the HELK server in ESXi. Based on the requirements, I decided to give it 16GB of RAM and a 200GB hard drive. I’ve got the space, though that means it will be living on spinning disks instead of my SSDs.
Next, I added my Ubuntu 16.04 Server ISO to its disk drive.
Once the machine booted, I went through a standard Ubuntu installation.
I then updated all the installed packages, just to prevent any headaches down the road.
Finally, I gave my new server a static IP address in my router.
With the VM configured, I pulled down the HELK repository.
Next, I ran the helk_install.sh script.
Like the documentation specified, you can keep an eye on the progress via /var/log/helk-install.log.
Once the install was complete, I was able to visit my Kibana dashboard using the provided URLs/credentials!
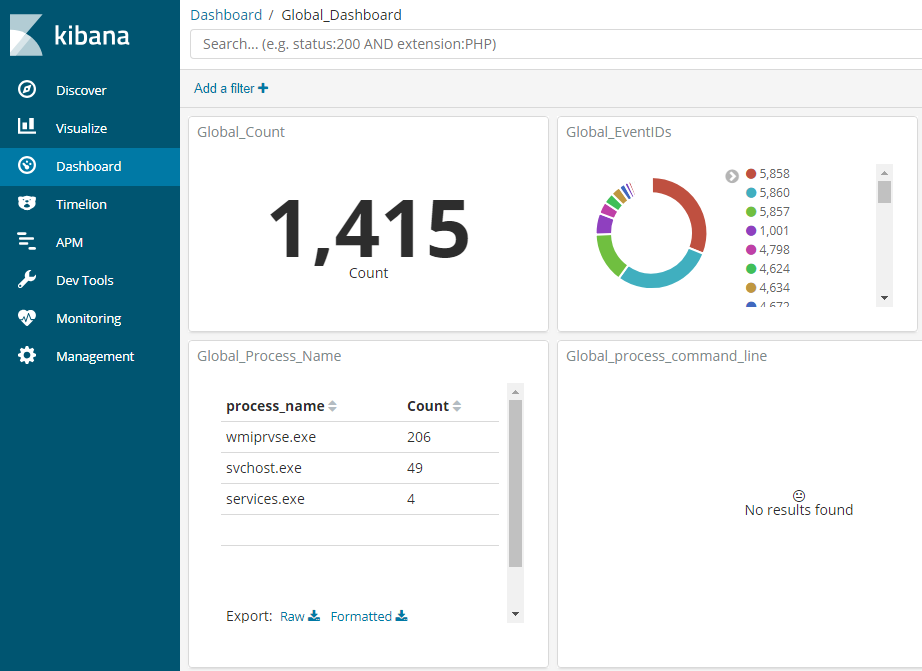
While I still have some more blog posts planned for feeding the HELK, I wanted to offer a small preview of what it looks like after ingesting some logs.
This is a quick example of my HELK installation being fed by Sysmon and Winlogbeat.
The HELK installation process was incredibly easy, and I’m excited to start hunting myself.
My goal is to configure and automate an entire Windows domain lab for both offensive and defensive purposes. If you have any recommendations or tips on using Terraform, then I’d love to hear them.
Stay tuned for some upcoming posts on Sysmon, Winlogbeat, and actually using HELK!
Ray Doyle is an avid pentester/security enthusiast/beer connoisseur who has worked in IT for almost 16 years now. From building machines and the software on them, to breaking into them and tearing it all down; he’s done it all. To show for it, he has obtained an OSCE, OSCP, eCPPT, GXPN, eWPT, eWPTX, SLAE, eMAPT, Security+, ICAgile CP, ITIL v3 Foundation, and even a sabermetrics certification!
He currently serves as a Senior Staff Adversarial Engineer for Avalara, and his previous position was a Principal Penetration Testing Consultant for Secureworks.
This page contains links to products that I may receive compensation from at no additional cost to you. View my Affiliate Disclosure page here. As an Amazon Associate, I earn from qualifying purchases.