Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
I know it’s a bit late, but I wanted to finally release my SLAE review!
Before I begin this week’s post, I just wanted to add a quick note.
This is actually my 200th consecutive post since deciding to post once a week!
I’m very proud of this milestone, and hope to continue posting for years to come.
For reference, the first post in this streak was my eCPPT review, which shows how far I’ve come.
Unless you haven’t been following along, I’ve made a ton of posts about my SLAE progress and assignments.
I went into this course with the vaguest of assembly knowledge. For example, I knew that there was a stack, which was first-in-last-out (FILO). I also knew that MOV would move things, JMP would jump, etc.
Other than that, I knew that I wanted to overwrite EIP, and normally jump to ESP. I had never written assembly by hand, so I figured this was the class for me.
Module 1 focuses on the basics of assembly, from instructions and registers to the standard library. This was the important part of the course for me, coming in with zero assembly knowledge.
That said, Vivek does a great job of explaining the concepts, and working through an exercise.
There is still plenty that I learned in the second module, the exam, and even my OSCP. That said, this module definitely laid a solid foundation for my assembly knowledge.
I took a ton of notes, and still reference my Evernote documentation from time to time. That said, I do recommend working through the exercises manually though, so you understand what is going on.
I even added a few scripts and snippets of my own to the material, which you can find in my GitHub repository!
Note that the basic SLAE course is only 32-bit, but most of the concepts carry over fairly easily to 64-bit assembly.
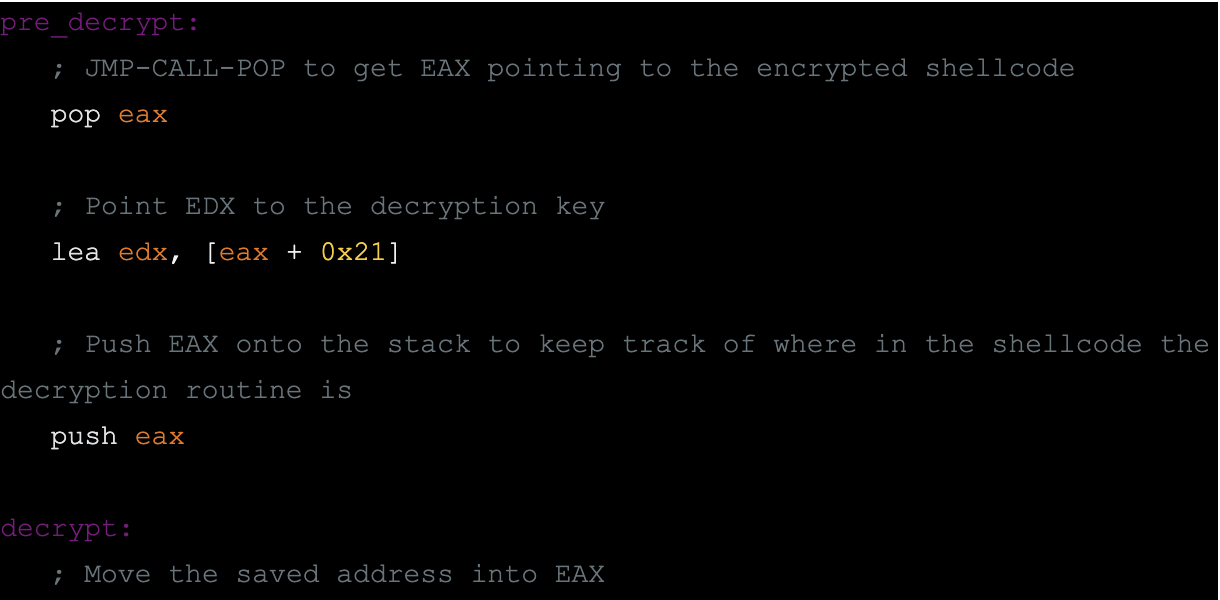
Next, module 2 builds on that assembly knowledge by teaching shellcoding.
You start the module with a shellcoding explanation, and shellcoding basics. After that, you convert some of your earlier assembly code into shellcode.
With this in place, the course moves into encoding, decoding, analysis, and crypters.
This section moves a lot faster than the first section, but is definitely the meat of the course.
You will want to manually write a lot of the code in this section, as Vivek moves through some of it quickly.
I’ve even managed to use some custom encoding during an engagement recently, which was awesome. I’ve been able to manually bypass AV with some of my payloads, even during the OSCE!
The SLAE Exam had three main requirements:
Vivek evaluated the assignments based on originality, and quality of explanation. Each assignment could earn up to 10 points, with 50 points required to pass.
Additionally, you can earn extra points for more new shellcodes, submission to Exploit Database, or community interaction on Twitter/Facebook/blog.
They say it takes about 5 working days for a result, but I think I got mine even faster than that.
The nice part about this course, is that you can take the exam on your own time.
That said, I was able to go through it fairly quickly, even while traveling to DEF CON 26 and DerbyCon 8.
Also, it was nice to space out my exam posts once a week. This allowed me to catch up on other posts, as it wasn’t taking me one week for each assignment.
I recommend taking the exam, and not just going through the course material. I learned a bunch during the exam, and even ended up with a few tricks to add to my toolbox.
You can find the seven exam posts that I submitted below, along with an accompanying write-up and solution code.
I also made a few other posts here and there, during the coursework itself. I wanted to share those here as well, if you wanted to go back and read through my processes.
Finally, for the community interaction piece of the exam, I continued to use my Twitter account. I got a ton of interaction, and some really good questions or answers to my questions. If you want to look back at any of these, then you can find them below.
If you want, then you can download all of my code from the GitHub repository.
The only changes I plan on making are the actual shellcodes that I re-submit to the Exploit Database.
In conclusion, this course was awesome, and easily worth the money. This was also my first PentesterAcademy course, so I plan on looking into some more.
If you are already quite familiar with x86 assembly, then you can probably skip the first module. If not, then this course will give you all the instruction that you will need.
For another great review/summary, I recommend the rcesecurity post.
If you have any suggestions for another certification to pursue, then I’d love to hear them!
Ray Doyle is an avid pentester/security enthusiast/beer connoisseur who has worked in IT for almost 16 years now. From building machines and the software on them, to breaking into them and tearing it all down; he’s done it all. To show for it, he has obtained an OSCE, OSCP, eCPPT, GXPN, eWPT, eWPTX, SLAE, eMAPT, Security+, ICAgile CP, ITIL v3 Foundation, and even a sabermetrics certification!
He currently serves as a Senior Staff Adversarial Engineer for Avalara, and his previous position was a Principal Penetration Testing Consultant for Secureworks.
This page contains links to products that I may receive compensation from at no additional cost to you. View my Affiliate Disclosure page here. As an Amazon Associate, I earn from qualifying purchases.